Performance Optimization
Helps manage requests such as compressing files. (Compression) or request routing adjustment to make the response faster

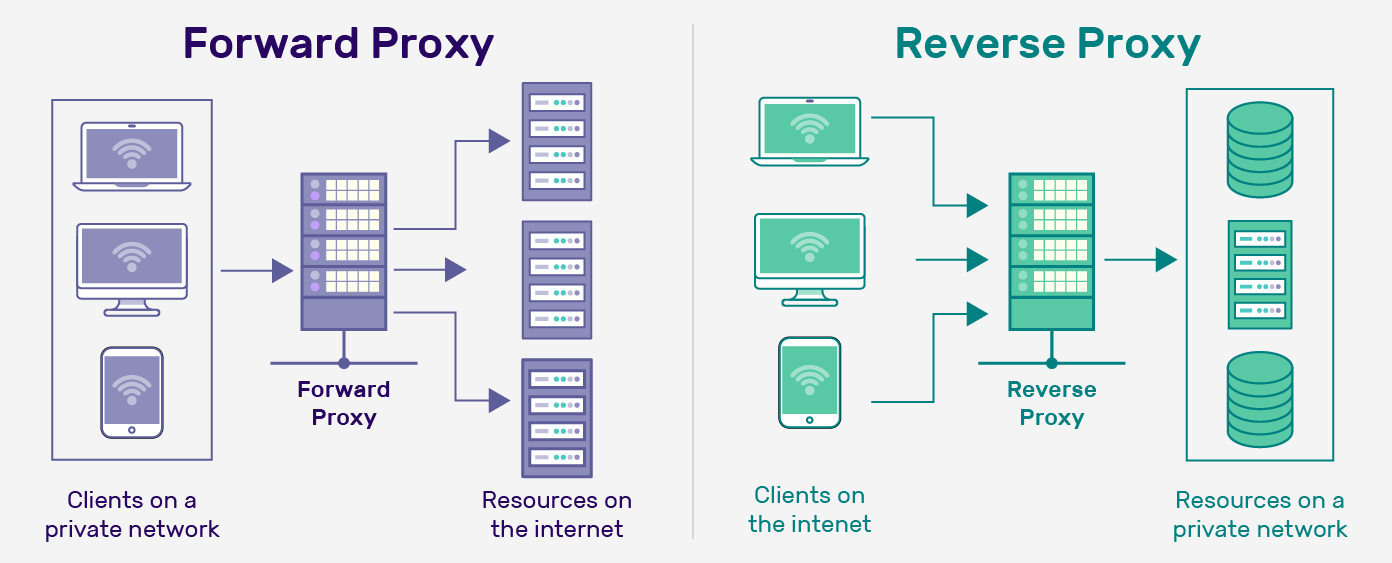
Reverse proxy is mainly used by server admins to achieve load balancing and high availability. A website may have several web servers behind the reverse proxy. The reverse proxy server takes requests from the Internet and forwards these requests to one of the back-end web servers. Most visitors don’t know websites are using reverse proxy because they usually lack the knowledge and tools to detect it or they simply don’t care about it.

Helps manage requests such as compressing files. (Compression) or request routing adjustment to make the response faster

Reverse Proxy can conceal the IP Address of the originating server that is difficult to connect to by malicious actors such as DDoS Attacks

Reverse Proxy can cache data to reduce the number of requests that must go to the origin server. Makes web pages or applications load faster

It helps distribute the load of requests across multiple servers in the system. This is to prevent overloading of one of the servers. and increase system stability
A reverse proxy is a server that sits between a client and backend servers, forwarding client requests to the appropriate backend and delivering the server's response back to the client. It acts as a security, performance, and scalability layer in many modern web architectures
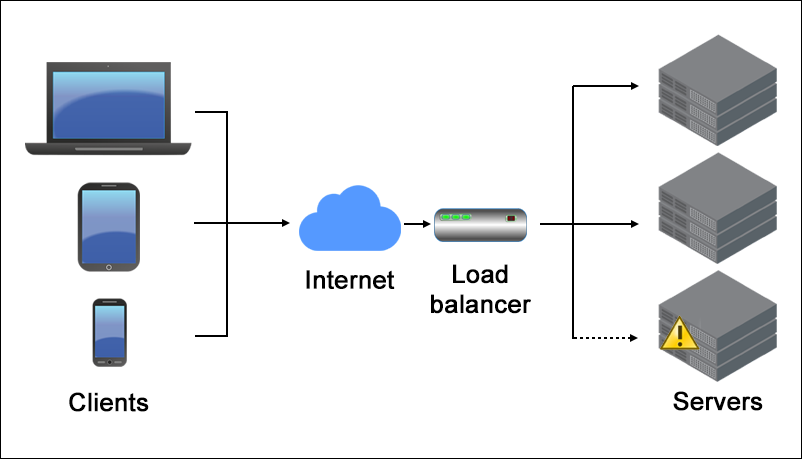
Scenario: An e-commerce platform experiences heavy traffic during holiday sales. Solution: A reverse proxy like NGINX or HAProxy distributes incoming traffic across multiple backend servers to prevent server overload

Scenario: A financial services website needs to protect backend servers from direct internet exposure. Solution: A reverse proxy masks backend server IP addresses and implements security measures such as DDoS protection
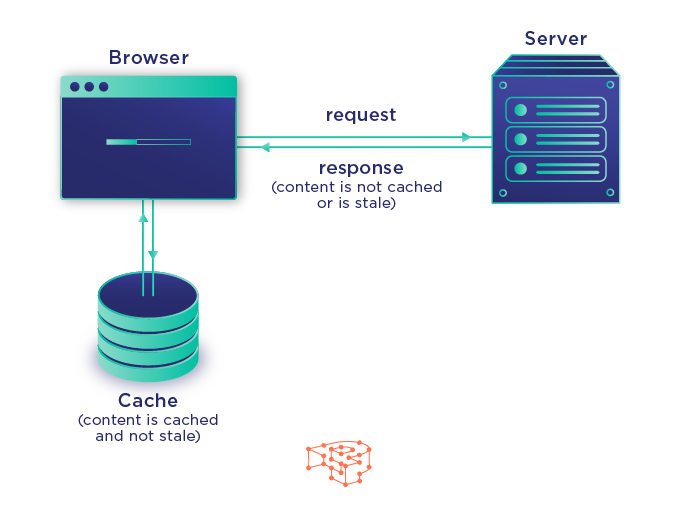
Scenario: A news website has frequent requests for static content such as images and articles. Solution: The reverse proxy caches frequently requested resources reducing the need to repeatedly
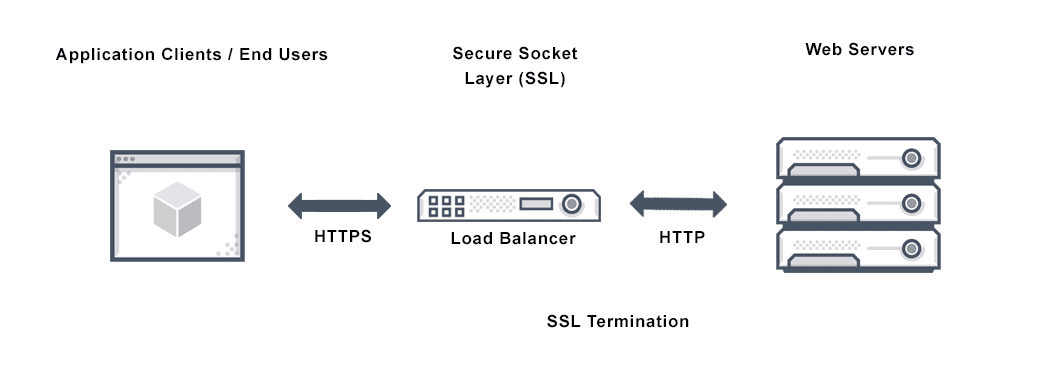
Scenario: A large SaaS company needs to manage multiple secure connections efficiently. Solution: The reverse proxy handles SSL/TLS encryption and decryption offloading the workload from backend servers
Working in this way allows for more efficient resource management and improves system security.
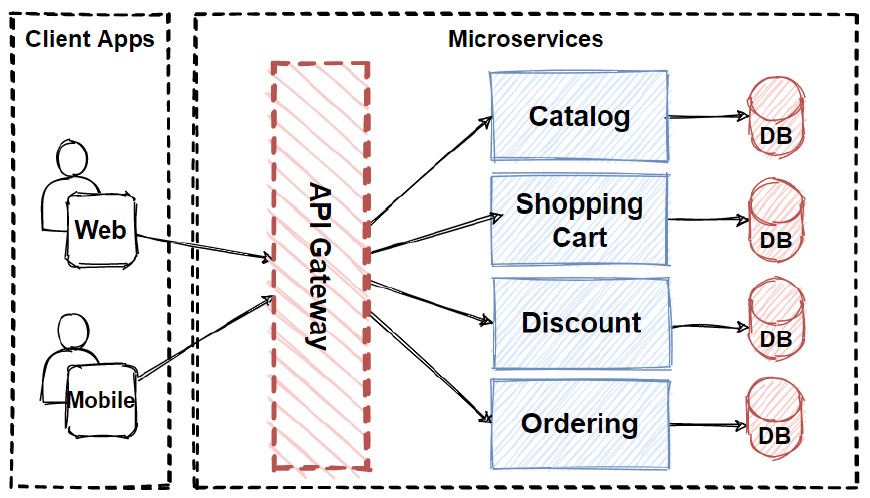
Large websites with many users such as e-commerce or social media platforms, often use reverse proxies to distribute load and improve service efficiency
Reverse Proxy helps manage API requests and filters out unauthorized requests. To ensure secure access to the system
Access to freedom of information on the internet is not just a right. But it is something that can create opportunities and the power to change the world. Having a clear plan to preserve and promote this freedom will allow you to connect and learn safely and without limits.
Using the Service allows you to access restricted websites and information in a secure and private manner
Data encryption helps prevent eavesdropping by outsiders. Including preventing privacy violations
Open source solutions allow you to perform your own security audits without having to rely on a third-party service that may have limitations

A reverse proxy is a server that sits between client devices and backend servers, forwarding client requests to the appropriate server and then sending the server’s response back to the client. Unlike a forward proxy that operates on behalf of the client, a reverse proxy handles traffic on behalf of servers, making it a critical component in web architecture
When a user makes a request to access a website or an application, the request first hits the reverse proxy server. The reverse proxy determines the appropriate backend server to handle the request and forwards it accordingly. After the backend server processes the request, it sends the response back to the reverse proxy, which then relays the information to the client.
It helps increase the security of the system in many ways. But the level of security depends on the proper installation and configuration methods. This includes selecting highly secure software and continually updating it.